
Preamble
Google Authenticator also offers HMAC-based One-Time Password (HOTP) as an alternative, generating OTPs based on a counter instead of time.
Users can back up their Google Authenticator settings for recovery in case they lose their phone.
Many other apps and services use similar TOTP or HOTP algorithms for 2FA, not just Google Authenticator.
Google Authenticator is commonly used for logging into our accounts when 2-factor authentication is enabled. How does it guarantee security?
Google Authenticator is a software-based authenticator that implements a two-step verification service. The diagram below provides details.
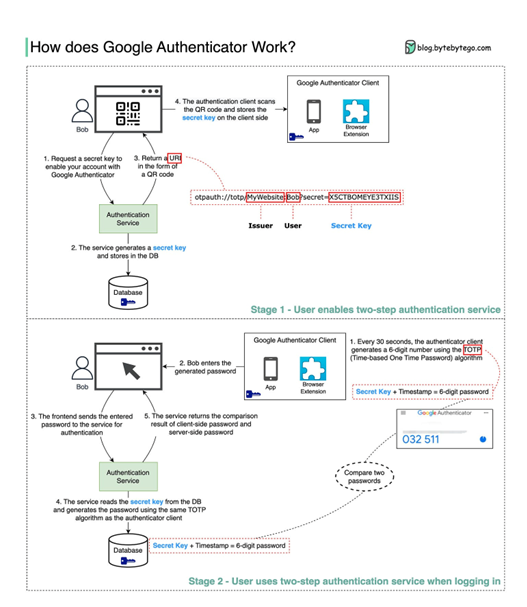
The two stages involved.
Stage 1 – Enabling Google’s two-step verification (2FA)
Steps 1 and 2: After installing Google authenticator App, Bob opens the web page to enable two-step verification. The front end requests a secret key. The authentication service generates Bob’s secret key and stores it in the database.
Step 3: The authentication service returns a URI to the front end. The URI comprises a key issuer, username, and secret key. The URI is displayed as a QR code on the web page. This step links the app to Bob’s online accounts.
Step 4: Bob then uses Google Authenticator to scan the generated QR code. The secret key is stored in the authenticator.
Stage 2 – The user uses the authenticator to log in
Steps 1 and 2: Bob wants to log into a website with Google two-step verification. For this, he needs the password. Every 30 seconds, Google Authenticator generates a 6-digit password using the TOTP (Time-based One Time Password) algorithm. Bob uses the password to login to the website.
Steps 3 and 4: The front end sends Bob’s password to the backend for authentication. The authentication service reads the secret key from the database and generates a 6-digit password using the same TOTP algorithm as the client.
Step 5: The authentication service compares the two passwords generated by the client and the server and returns the comparison result to the front. Bob can proceed with the login process only if the two passwords match.
Why should we believe this authentication mechanism in secure?
• The main advantage of TOTP is that the OTPs are unique and only valid for a short time (usually 30 seconds), making them difficult to steal or predict.
• Can the secret key be obtained by others?
We need to make sure the secret key is transmitted using HTTPS. The authenticator client and the database store the secret key, and we must ensure the secret keys are encrypted.
• Can the 6-digit password be guessed by hackers?
No. The password has six digits, so the generated password has 1 million potential combinations. Plus, the password changes every 30 seconds. If hackers want to guess the password in 30 seconds, they must enter 30,000 combinations per second.
• Even if someone intercepts the password, they’ll need physical access to the user’s phone or the QR code/secret key to generate the correct OTP and log in.
